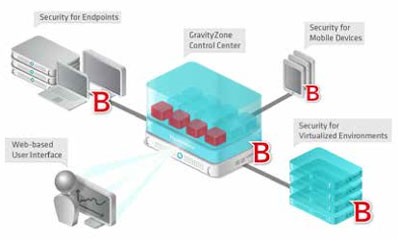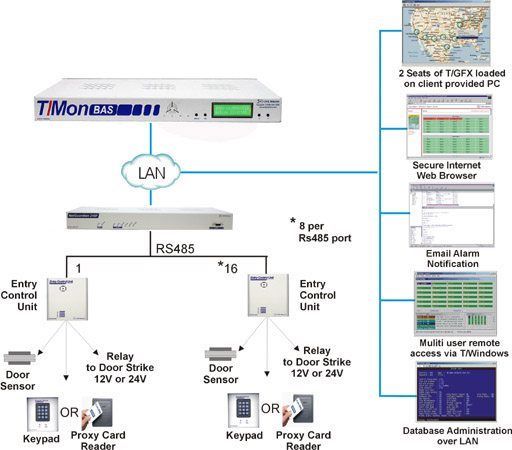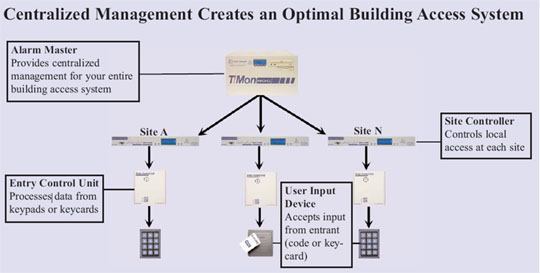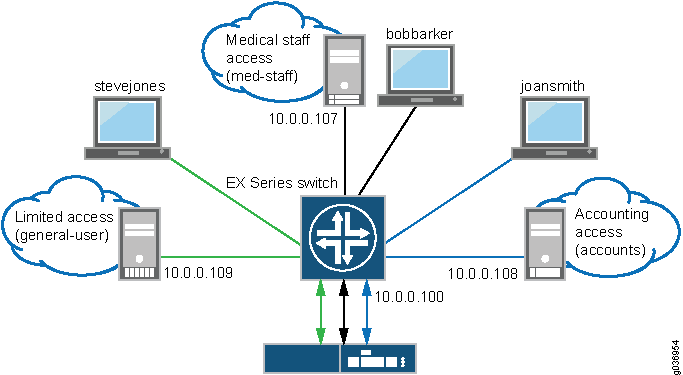
Example: Configuring Centralized Access Control to Network Resources, with an EX Series Switch Connected to Junos Pulse Access Control Service - TechLibrary - Juniper Networks
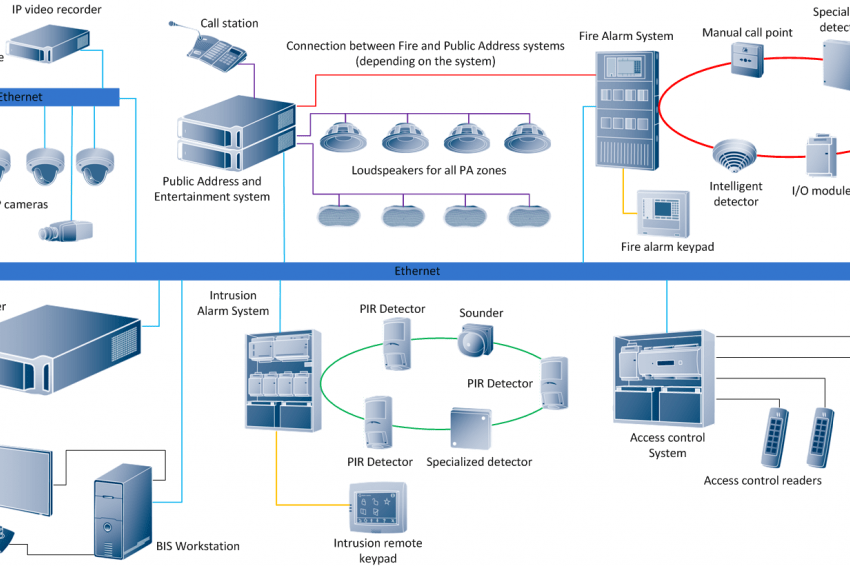
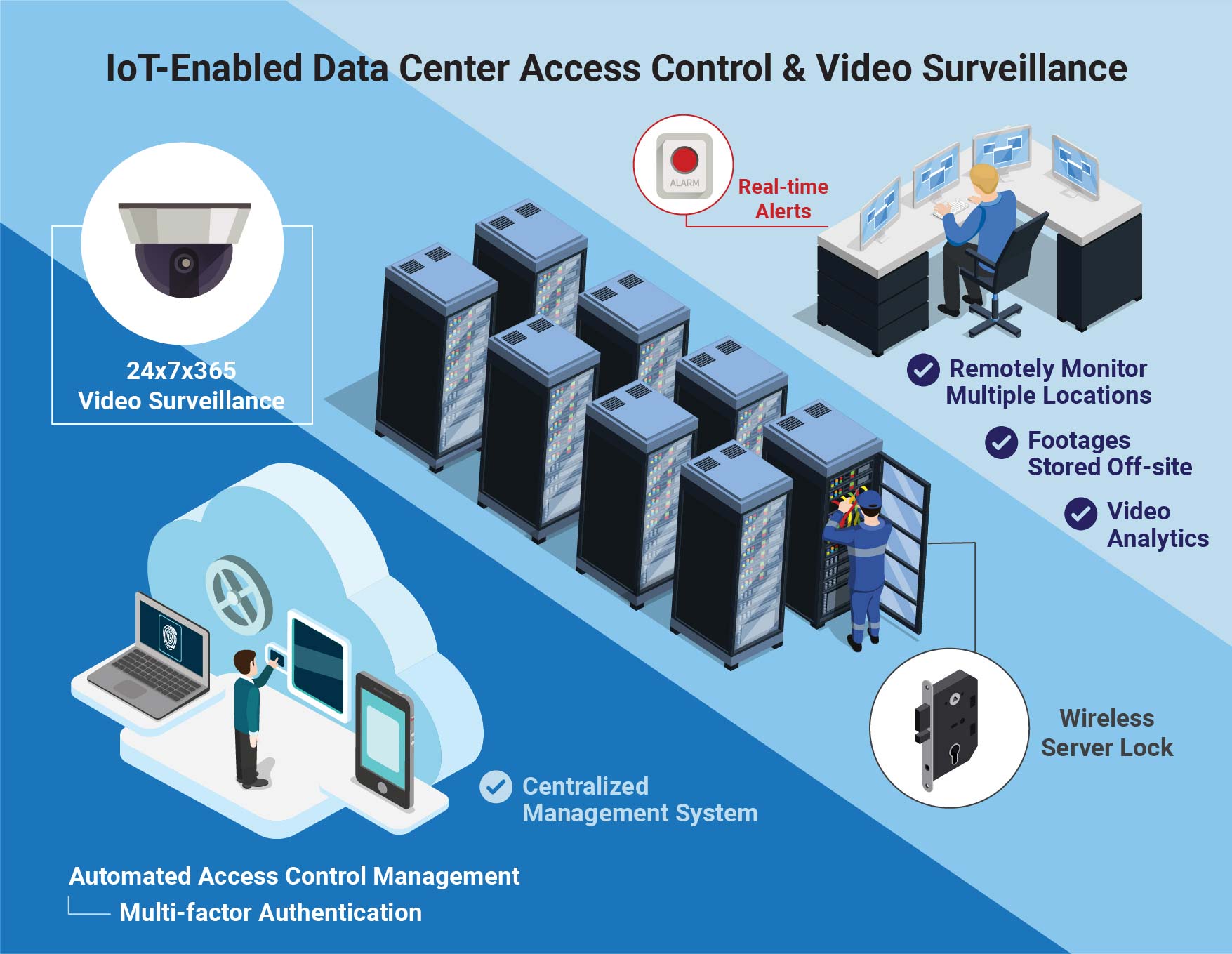
Achieving End-to-End Fire Security in High-Rise Buildings | GIT-SECURITY.com – Portal for Safety and Security

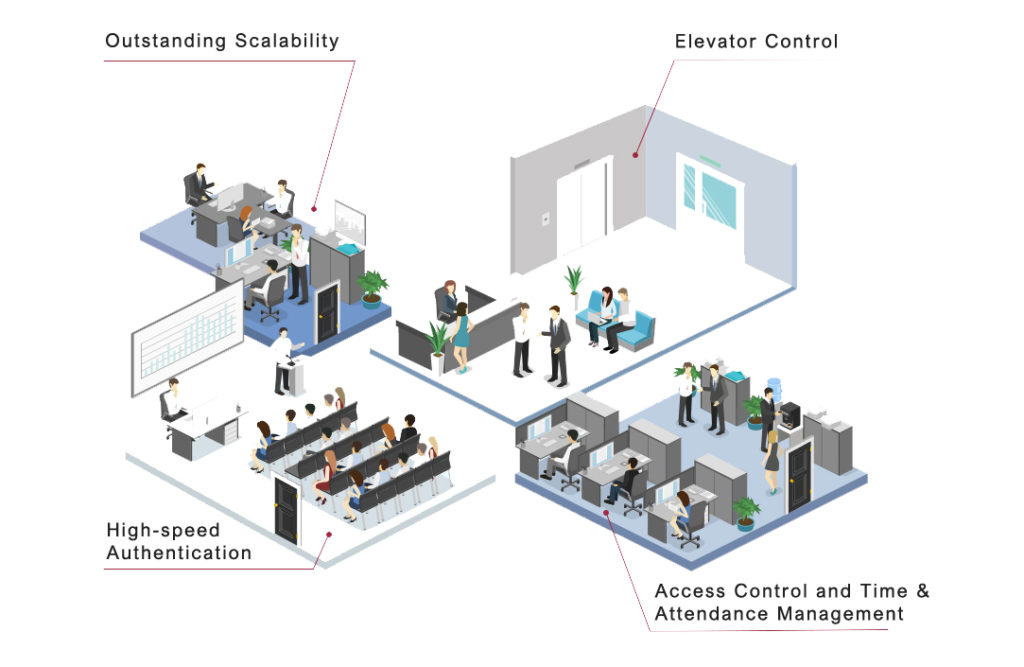
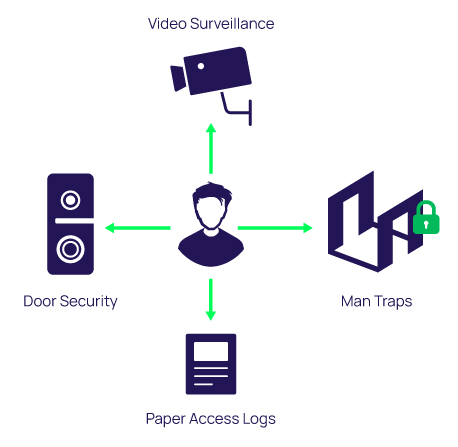
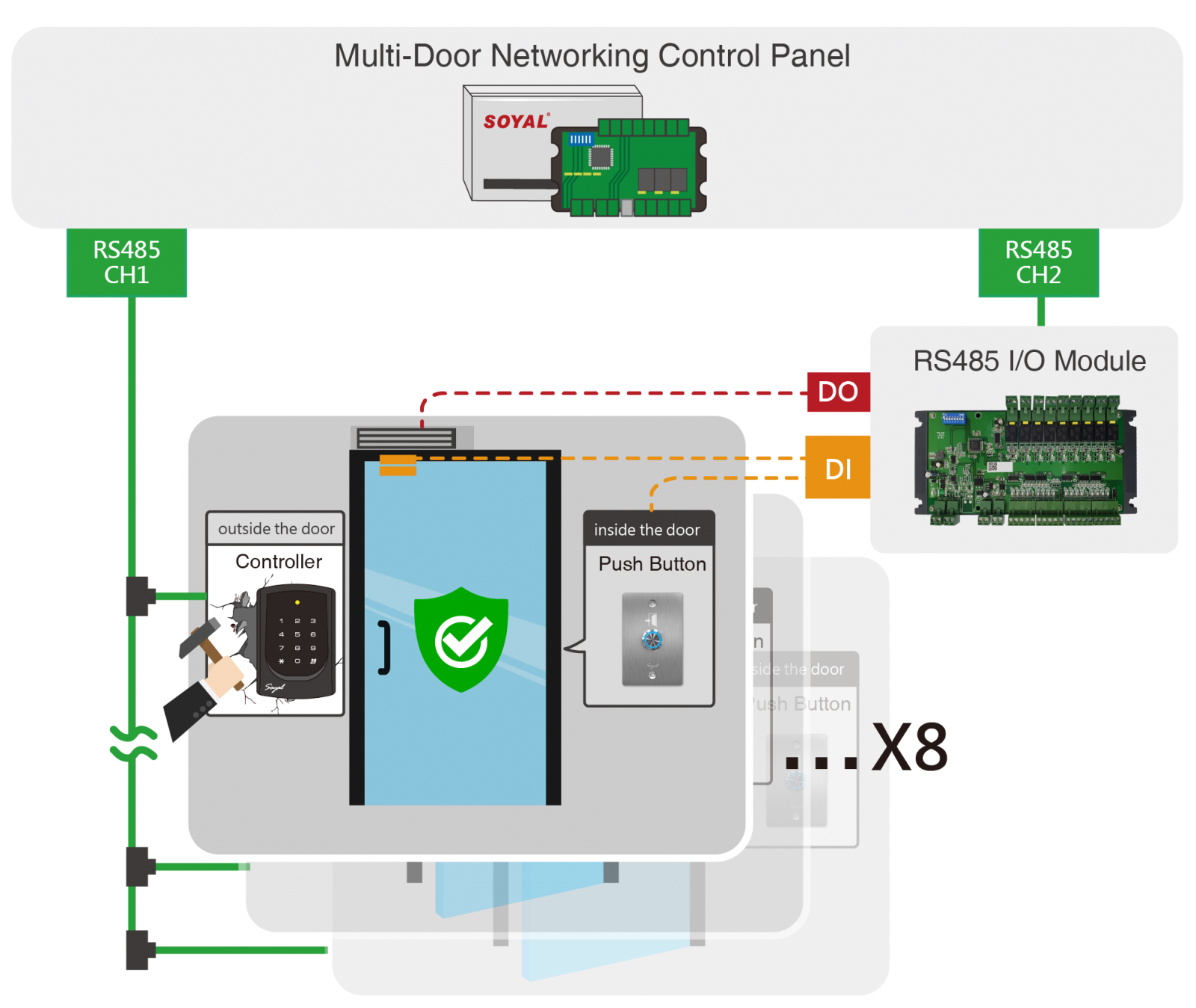
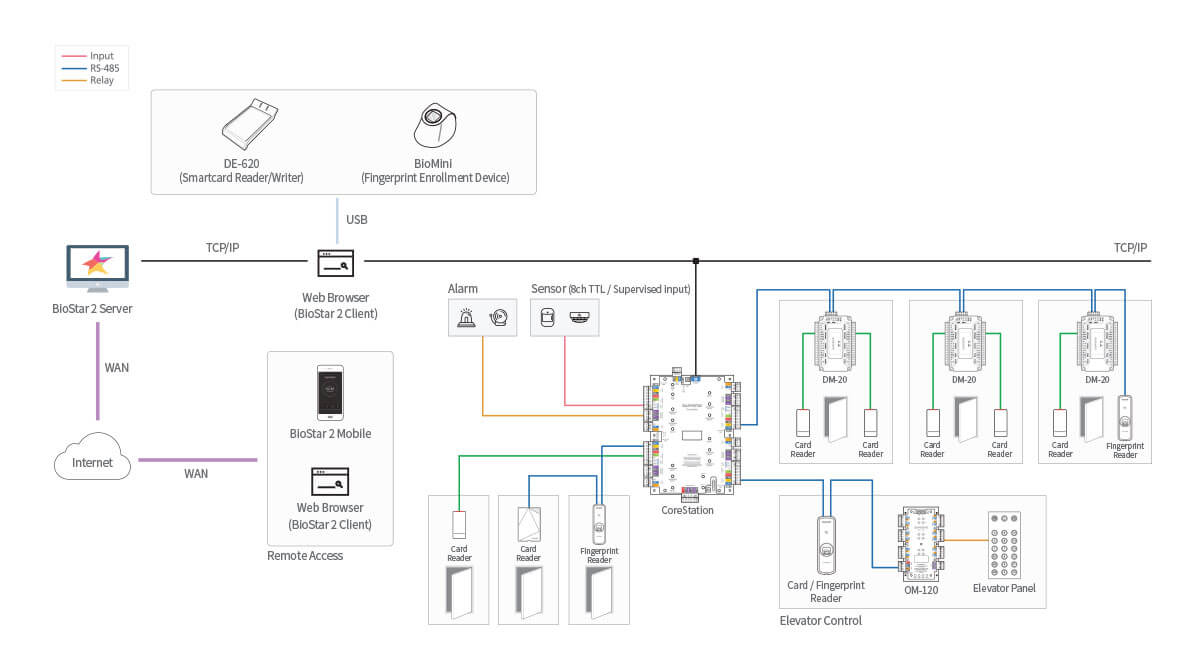
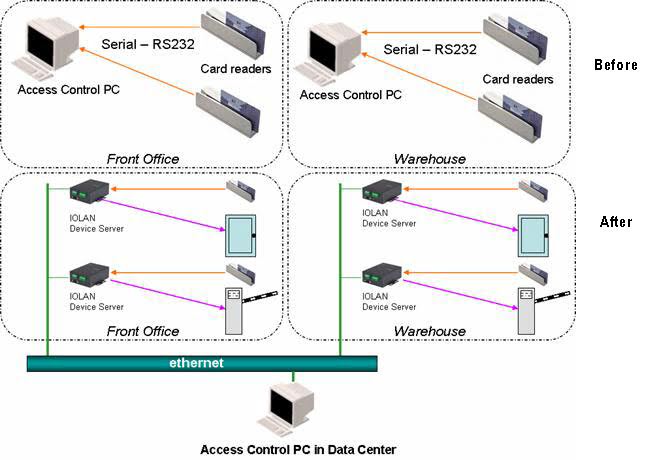
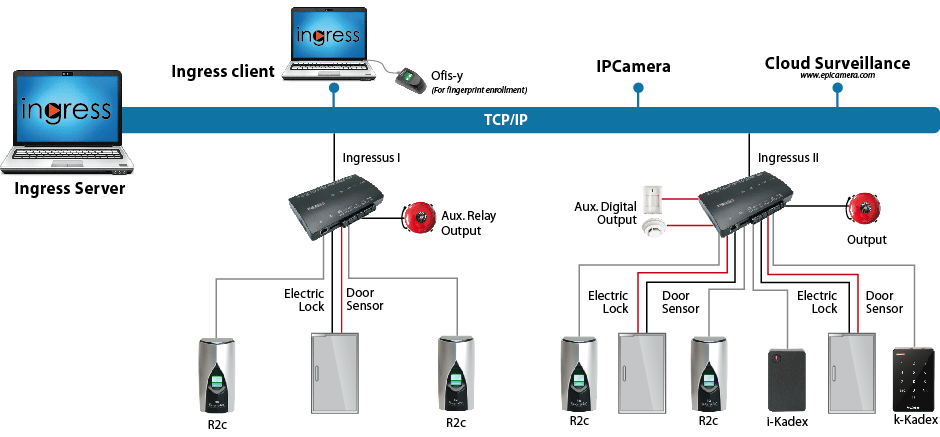
Centralized access control system with card reader - COMPACT - OMNITEC SYSTEMS, S.L. - building / for hotel